
In today’s digital age, organizations across all industries hold a treasure trove of sensitive data: financial records, intellectual property, student information, and even national security secrets. Protecting this data is paramount, and a critical line of defense lies in a seemingly mundane task – User Access Reviews (UARs).
But what happens when UARs are neglected or treated as a box-checking exercise? The consequences can be dire, leading to a costly and potentially devastating security breach. Let’s delve into the high cost of skipping UARs and explore why they’re a crucial security investment.
The Insider Threat: A Looming Danger
While external attacks grab headlines, a significant and often underestimated threat lurks within your organization: the insider threat. Disgruntled employees, accidental insiders due to human error, or even collaborators with malicious intent can exploit weak access controls to steal data, commit fraud, or disrupt critical systems.
According to the Ponemon Institute’s 2023 Cost of a Data Breach Report:
• The average cost of a data breach caused by malicious insiders is a staggering $4.87 million USD.
• A single data breach can cripple an organization’s reputation, erode customer trust, and result in hefty regulatory fines, potentially reaching tens of millions of dollars depending on the severity of the breach.
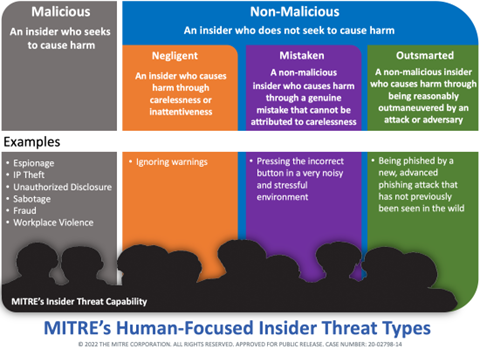
UARs: Your Security Shield
So, how do UARs mitigate these risks? Imagine a situation where a disgruntled employee in your IT department has access to modified user privileges. Skipping UARs means this access may not be reviewed, leaving a gaping hole in your security posture. A timely UAR, however, could identify this anomaly and revoke unnecessary access, preventing a potential insider attack.
Here’s how UARs act as a security shield:
• Reduce Privilege Creep: Over time, user access rights can accumulate, creating situations where employees have access to data or systems beyond their current job duties. Regular UARs help identify and eliminate unnecessary access privileges.
• Enhance Compliance: Many industries have strict data privacy regulations requiring organizations to maintain appropriate access controls. UARs provide a documented audit trail, demonstrating your commitment to compliance.
• Mitigate Human Error: Accidental data breaches can occur due to human error, such as granting access to the wrong person or forgetting to revoke access when an employee leaves the company. UARs minimize these risks by establishing a systematic review process.
The True Cost of Inaction
The financial impact of skipping UARs extends far beyond the immediate cost of a data breach. Consider the following:
• Lost Productivity: A cyberattack can bring your operations to a standstill, leading to lost productivity and significant revenue losses. A study by the Ponemon Institute found that a single hour of downtime can cost a financial institution an average of $8,200 per second.
• Reputational Damage: A data breach can shatter your organization’s reputation, eroding customer trust and potentially leading to a decline in sales. Rebuilding trust can take years and significant investment in public relations efforts.
• Legal Costs: Data breaches can trigger legal action from affected individuals or regulatory bodies, leading to hefty fines and settlements.
The Takeaway: Invest in Security, Invest in UARs
Skipping UARs is a gamble that simply isn’t worth taking. By implementing a robust UAR program, you can significantly reduce the risk of insider threats, data breaches, and the associated financial consequences.
Ready to learn more about how BAAR’s UAR solutions can help you secure your organization and safeguard your valuable data? Contact us today for a free consultation and let’s discuss how we can build a watertight security posture for your organization.
Don’t wait for a costly data breach to act. Invest in UARs, invest in your security, and invest in peace of mind.
Sources:
• Ponemon Institute: https://www.ponemon.org/ (2023 Cost of a Data Breach Report)
• IBM Security X-Force Threat Intelligence Index: https://www.ibm.com/downloads/cas/ADLMYLAZ



