The ever-evolving threat landscape necessitates robust cybersecurity measures, especially for organizations entrusted with sensitive information. The Department of Defense (DoD) understands this criticality, and to address these concerns, they’ve implemented the Cybersecurity Maturity Model Certification (CMMC) 2.0 program. At BAAR Technologies, a leader in Identity Access Management (IAM), Governance and Administration (IGA), and control assurance solutions, we’re dedicated to keeping you informed about regulations that impact your business.
CMMC 2.0: Building Upon the Foundation
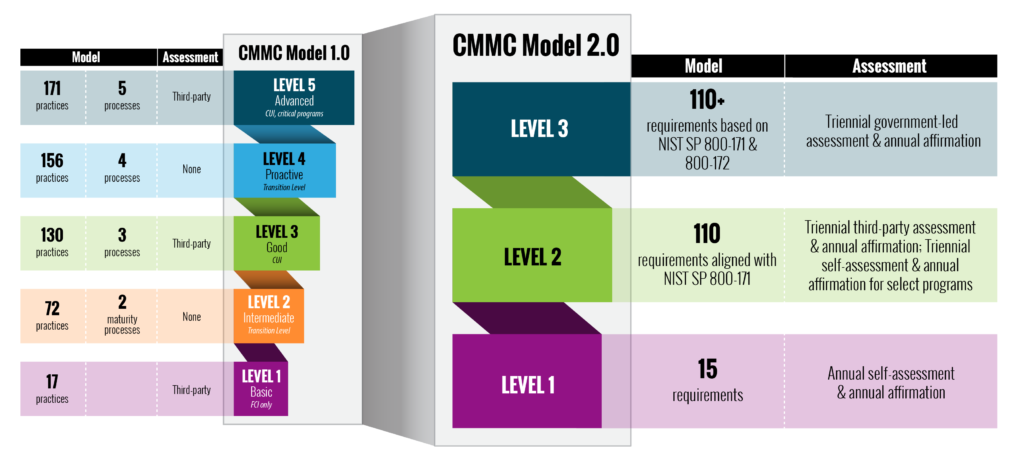
CMMC 2.0 is the successor to the original CMMC program, offering a streamlined and more practical approach to cybersecurity assessment and certification. While both programs share the objective of protecting sensitive information within the Defense Industrial Base (DIB), CMMC 2.0 introduces several key differences:
• Reduced complexity: CMMC 2.0 consolidates the five maturity levels of CMMC 1.0 into three streamlined levels, making compliance more accessible for organizations.
• Focus on self-assessment: CMMC 2.0 allows organizations to conduct self-assessments for specific levels, reducing reliance on third-party assessments and associated costs.
• Alignment with NIST standards: CMMC 2.0 requirements directly map to the well-established National Institute of Standards and Technology (NIST) Special Publications (SP) 800-171 series, simplifying implementation for organizations already familiar with these standards.
CMMC 2.0 Levels: Defining Your Cybersecurity Posture
CMMC 2.0 outlines three distinct levels, each requiring a progressive level of cybersecurity maturity:
• Level 1: Foundational: This level establishes a baseline of cybersecurity practices essential for safeguarding Controlled Unclassified Information (CUI). It emphasizes fundamental controls like access controls, password management, and malware protection to prevent basic cyber threats and minimize the potential for inadvertent data breaches.
• Level 2: Advanced: Building on Level 1’s foundational controls, Level 2 mandates additional security measures to strengthen an organization’s overall cybersecurity posture. This level requires implementing an incident response plan to manage and recover from security incidents effectively and system monitoring to detect and promptly address potential threats. Additionally, Level 2 emphasizes security awareness training to educate employees on cybersecurity best practices and their role in protecting sensitive information.
• Level 3: Expert: The most comprehensive level, Level 3, demands a sophisticated and continually improving cybersecurity program. This level necessitates ongoing professional assessments to objectively evaluate an organization’s cybersecurity posture against the CMMC 2.0 requirements. Level 3 also mandates continuous monitoring to proactively identify and mitigate vulnerabilities, ensuring the organization remains adaptable and resilient in the face of evolving cyber threats.
CMMC 2.0 Assessments: Ensuring Compliance
CMMC 2.0 utilizes two primary assessment methods:
• Self-assessment: Organizations can conduct self-assessments for Level 1 and potentially Level 2, leveraging standardized questionnaires and documentation requirements.
• Government-led assessments: Independent assessors, approved by the CMMC Accreditation Body (CMMC-AB), conduct on-site assessments for Level 3 and potentially Level 2, depending on the specific circumstances.
Who Needs to Comply with CMMC 2.0?
If your organization interacts with the DoD supply chain in any capacity, CMMC 2.0 compliance might be mandatory. This includes:
• Prime contractors: Companies directly awarded DoD contracts are responsible for ensuring their own cybersecurity compliance and that of their subcontractors down the supply chain.
• Subcontractors: Organizations of any size that support prime contractors in fulfilling DoD contracts must also comply with CMMC 2.0 requirements. This ensures that sensitive information is protected throughout the entire supply chain, from the prime contractor down to lower-tier subcontractors.
• Small businesses: Regardless of size, any business working within the DoD supply chain, even if they are not directly awarded a DoD contract, must still adhere to CMMC 2.0 guidelines. This is because they may still handle or transmit CUI as part of their work for a prime contractor or subcontractor.
Protecting What Matters: Controlled Unclassified Information (CUI)
CMMC 2.0 prioritizes the protection of Controlled Unclassified Information (CUI). This category encompasses sensitive information that is not classified but still requires safeguarding due to its national security significance. Examples of CUI include technical data, contract information, and logistics details related to DoD programs.
BAAR Technologies: Your Partner in CMMC 2.0 Compliance
BAAR Technologies, with its expertise in IAM, IGA, and control assurance, is here to assist you in navigating the CMMC 2.0 landscape. We offer solutions that can help you:
• Implement robust access controls to safeguard CUI and prevent unauthorized access.
• Strengthen password management practices to minimize password-related security vulnerabilities.
• Deploy multi-factor authentication (MFA) solutions like the BAAR mobile authenticator for an additional layer of security.
• Develop and implement comprehensive incident response plans to effectively manage cyber threats and minimize potential damage.
By partnering with BAAR Technologies, you can achieve and maintain CMMC 2.0 compliance with confidence, ensuring the security of sensitive information and preserving your competitive edge within the DIB.
Stay tuned for future blog posts where we delve deeper into specific CMMC 2.0 requirements and how BAAR’s solutions can empower your organization to meet and exceed compliance standards.
Explore how BAAR Technologies Inc. can secure your cyber future—visit us now at www.baar.ai.